SOC 2 compliance is important for service organizations that want to protect their customers’ data. For example, organizations that use a Software-as-a-Service (SaaS) vendor can use SOC 2 to verify that their vendor meets specific security requirements.
Recent data protection laws have entrenched the rights of individuals to privacy and the security of their personal data across the globe.
As personal information becomes more valuable, the frequency and severity of security breaches only increase. Organizations that do not adequately secure their data face the loss of their reputation, but also potentially devastating fines.
Companies are therefore wondering which compliance agreement would be best suited for their organization. At different levels of government, there are regulations in place that define data protection and prescribe stiff penalties for non-compliance.
Here are a few examples, among many:
- In the United States, HIPAA requires healthcare organizations to protect the confidentiality of patient records and medical information.
- In Canada, PIPEDA governs how private companies can collect, use and disclose personal information in the course of commercial activities.
- Internationally, the Payment Card Industry Data Security Standard (PCI DSS) establishes specific standards regarding the protection of account and cardholder data.
- As for the European Union, the general data protection regulation ( RGDP) is based on an individual’s “Right to be forgotten” and prescribes data protection and privacy for all individuals living within its territory. Fines for non-compliance can be up to 4% of total annual income.
With so many regulations, standards, and certifications, it’s no wonder businesses are confused. Industry standards and approaches have evolved to better protect the data for which they are responsible, yet their variety and complexity make it difficult to know where to begin.
While most have unique and particular requirements, when it comes to privacy and data protection, they all prescribe a common set of best practices.
With standards like the SOC 2 report or recognized certifications like ISO 27001, you’ll establish a solid information security foundation and your business will be continuously compliant with ever-changing requirements.
In this blog post, we will not only explain what SOC 2 compliance is, who it is for, what type of the third party performs a SOC 2 audit, and what its Type 1 and Type 2 trust service principles are, but also what are the main differences between SOC 1 and SOC 2 as well as the main advantages of SOC 2 compliance.
Contents
What is SOC 2 compliance?
Developed by the American Institute of Certified Public Accountants (AICPA), “Systems and Organizations Controls 2”, SOC 2 (or SOC II) is a framework used to help companies demonstrate the security controls that are in place to protect customer data in the cloud.
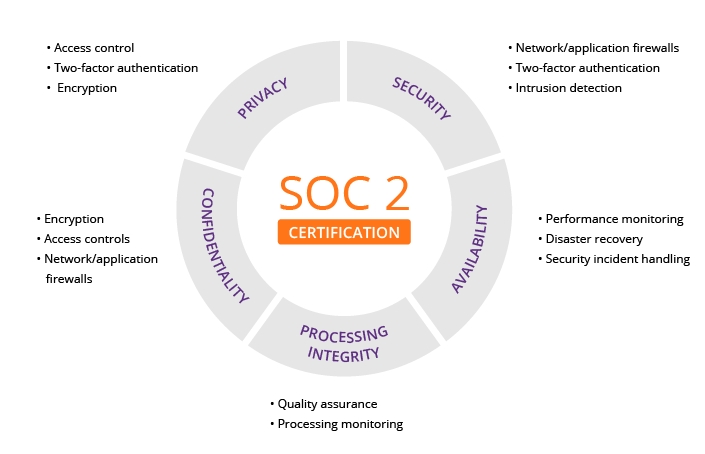
These controls became known as the Trust Services Principles: Security, Availability, Processing Integrity, Confidentiality and finally Privacy.
SOC 2 was created to give customers confidence that the service providers they use have adequate controls and security measures in place to protect their data.
Unlike the rigorous set of PCI-DSS security requirements, the SOC is more of a framework for organizations to design their own controls as long as they effectively adhere to the principles of trust.
SOC 2 compliance is considered the gold standard for cloud data security in terms of third-party assurance, helping you build trust with customers and reduce the risk of a data breach.
Also Read: 56 Marketing Tools + Resources To Increase Your Productivity
Importance of SOC 2 Compliance
Both SOC 1 and SOC 2 are compliance standards regulated by the AICPA. While SOC 1 aims to help organizations report on internal controls over their customers’ financial statements, SOC 2 is more general and assesses a given service provider’s controls for various TSCs, namely security, confidentiality, availability, processing integrity and confidentiality.
However, they have different purposes, types of control coverage, audiences, and intended uses, and they are not leveled against each other, as described in the following list:
-
Different types of control coverage
While the SOC 1 audit strictly covers the handling and protection of customer information in business and IT processes, the SOC 2 can cover all five principles, either a given selection of them or all five of them.
-
Different audit audiences
While the objective of the SOC 1 audit is to enable Certified Public Accountants (CPAs) in the management of an organization, external auditors and users to have confidence in the accuracy of its financial statements, the goal of the SOC 2 audit is to provide executives, business partners, and external auditors with an assessment of whether or not their company’s security measures meet industry standards.
-
Different uses foreseen by the audit
While SOC 1 helps user entities obtain the impact of service organization controls on their financial statements, SOC 2 helps oversee organizations, vendor management plans, internal corporate governance and management processes risks, as well as regulatory oversight.
You might need a SOC 1 or SOC 2 report if you are an organization hosting client systems, such as an infrastructure as a service (IaaS) or a platform as a service (PaaS), or a cloud hosting software, such as a software-as-a-service (SaaS) entity or data center.
Choosing between SOC 1 and SOC 2 should come down to:
a) the type of compliance requirements you are held to,
b) the type of assurance you need to provide to your customers,
c) and the type of information you are responsible for protection.
Who Does SOC 2 Apply To?
SOC 2 applies to any technology service provider or SaaS business that stores, processes, or transmits customer data, including cloud computing, and managed security.
It also includes healthcare claims management, processing, and automation providers of the sales force.
What are the main benefits of SOC 2 compliance?
SOC 2 compliance has many key benefits, including:
-
Secure business partnerships
SOC 2 compliance can help you build trust and secure business partnerships. If you are a SOC 2-compliant organization, your potential partners will know that you have the necessary controls in place to protect their data.
-
Improve your security measures
SOC 2 compliance can help you identify and improve your security measures in terms of technology and process, which means your organization will be better protected against cyberattacks.
-
Prevent incidents and financial losses
SOC 2 compliance can help you prevent incidents and financial losses that could damage your reputation or legal action against your organization.
-
Protect your brand image and reputation
SOC 2 compliance can help protect your brand image and reputation by demonstrating your commitment to protecting your customers’ data. With the latest corporate data breach news going on, showing a security compliance seal will help you earn and maintain customer trust.
-
Attract investors and buyers
SOC 2 compliance can help you attract potential investors and buyers because it demonstrates that you are a responsible and reliable company and that you also have the necessary controls in place to protect their investment.
-
Comply with requirements of other third parties
SOC 2 compliance can also help you comply with other requirements such as PCI-DSS, ISO 27001, and HIPAA, but also with the requirements of your customers and partners if they have SOC 2-related clauses in their contracts.
In short, SOC 2 reports are not just a regulatory compliance exercise for good measure, but also a valuable marketing tool for winning new business.
As noted in our other blog post detailing some of the above benefits of SOC compliance, starting your SOC 2 compliance journey early will allow your organization to thrive in an environment with tight controls, making all your future compliance projects faster and easier to do.
Also Read: SEO Content Writing vs Creative Content Writing- Comparison Guide 2024
What are the key controls of SOC 2?
The Service Organization Control 2 (SOC 2) set of compliance and auditing process requirements was created to help companies determine whether their business partners can properly secure data. This includes protecting the interests of customers from unauthorized access as well as maintaining confidentiality for everyone involved in the transaction process.
The 5 key security controls or Trust Services Criteria (TSC) of SOC 2 are described below:
- Security refers to the protection of information and systems from unauthorized access, use or disclosure, through the use of security systems or processes, including firewalls, encryption, and two-factor user authentication.
- Availability encompasses the accessibility of the system and data, in accordance with the terms specified and agreed upon in a contract or service level agreement (SLA), as well as the ability of the system to perform its required function at specified times.
- Processing integrity ensures that customer data is complete, valid, accurate, timely and authorized, and that processing is carried out in accordance with stated policies and procedures.
- Confidentiality relates to data considered confidential when its access or disclosure is limited to authorized persons, or when its unauthorized access or disclosure would have an adverse impact on customers.
- Privacy covers the collection, use, retention, and disposal of customer data in a manner consistent with an organization’s privacy policy and applicable laws and regulations.
What type of third party performs a SOC 2 audit?
A SOC 2 audit must be carried out by a qualified and independent third-party auditor, including CPA (Certified Public Accountant) firms.
The auditor will review the service organization’s SOC 2 report and issue a SOC 2 attestation report which will include the auditor’s opinion on whether the service organization has met the SOC 2 criteria.
What are SOC 2 Type 1 and Type 2?
Overall, SOC 2 compliance takes about six months with third-party assessors performing two separate audits. The SOC 2 Type 1 audit looks at the design and provides a snapshot of your security processes in place at that time.
The SOC 2 Type 2 audit, on the other hand, will verify the operational effectiveness of your internal controls over the long term. You must complete type 1 as a prerequisite for the type 2 attestation.
Let’s learn more about the differences between SOC 2 type 1 and type 2 and determine which to pursue on your path to compliance.
SOC 2 Type 1
SOC 2 Type 1 is a report on a service organization’s system and the suitability of the design of controls. The report describes the current systems and controls in place and reviews documents around these controls. Design sufficiency of all Administrative, Technical, and Logical controls are validated.
- The SOC 2 Type I report is an attestation of your company’s service organization’s controls at a specific time and certifies that these are properly designed and implemented.
- Expect this process to take about two months to allow for policy implementation, testing, and adjustment. Once completed, the booked assessment will typically involve employee interviews, walkthroughs, and a detailed review of submitted documentation.
- A SOC 2 Type 1 report will be generated once all necessary exception clarifications have been made.
- The SOC 2 Type I report is an attestation of your company’s service organization’s controls over a period of time and certifies that these are properly designed and implemented and are effective.
SOC 2 Type 2
A SOC 2 Type 2 report is an internal controls report capturing how a company safeguards customer data and how well those controls are operating. Companies that use cloud service providers use SOC 2 reports to assess and address the risks associated with third-party technology services.
- In general, SOC 2 Type 2 reports usually last at least six months, but can often take up to a year or more. This is due to many factors involved in the path to attestation, which may be due to company certification requirements that must be met.
- For example, if a company has a very diverse and extensive IT and cybersecurity infrastructure, the audit process will likely take longer than usual for a full SOC report. Other factors affecting the scope of the audit such as the type, location and number of users in the business (i.e. on-site and off-site) will greatly impact the process of attestation.
- Ultimately, though, the primary factor affecting the timeline for completing the SOC 2 process is the type of SOC 2 report your company has selected.
Also Read: 20 Best Nocode Development Platforms & Tools List 2024
Conclusion
Now more than ever, the continued success of your business depends on trust. Trust of your employees, your partners and especially your customers. SOC 2 compliance is the best way to ensure that trust.
Not only does this help secure your customer data, but it also helps differentiate your business in the marketplace. For any business that puts customer trust first, SOC 2 compliance is the way to go.
Complying early has several advantages, in particular, because it is much easier to meet the requirements when your company still has few employees and few departments. If you wait for your business to grow, the process will become much more complicated and expensive.
Another benefit of starting early is that your business will grow in an environment with tighter controls that will help make compliance assessments faster and easier to perform in the future, no matter the size of the business.
SOC 2 compliance is not a one-time event, but rather an ongoing journey that requires the commitment of the entire organization.
FAQs – SOC 2 Compliance
1. Is a SOC 2 Report HIPAA Compliant?
The answer is no, but SOC 2 compliance can also help you comply with other requirements such as PCI-DSS , ISO 27001 and HIPAA, but also with the requirements of your customers and partners if they have SOC 2-related clauses in their contracts.
In short, SOC 2 reports are not just a regulatory compliance exercise for good measure, but also a valuable marketing tool for winning new business.
There are several areas required by the HIPAA security rule that is not covered by a SOC 2. These include passwords, biometrics, physical security, transportation of PHI, and remote access.
To keep things simple, in this scenario we will compare a SOC 2 that only covers security criteria to a report that covers HIPAA security compliance.
2. What is the First Step Towards HIPAA Compliance?
The first step toward HIPAA Compliance is doing your research to determine if you are a covered entity. Once you determine that the HIPAA Security Rule applies to your organization, finding a reputable firm to assist in performing a readiness assessment is a great next step.
A readiness assessment will help identify gaps that need to be addressed prior to undergoing the HIPAA compliance audit and will assist you in creating a robust control environment.
3. How is SOC 2 Type 2 different than Type 1?
SOC 2 reports come in two flavors: Type 1 and Type 2. Here is the description of the differences between the two:
- The SOC 2 Type 1 report is a report on a service organization’s system and control design adequacy. The Type 1 report looks at a point in time on how the organization describes the system and controls in place. In addition, this review ensures that the controls described allowing the criteria to be met.
- The SOC 2 Type 2 report is similar to the Type 1 report, but the controls are described and evaluated for at least six months to see if they are operating as defined by management.

Director of Digital Marketing | NLP Entity SEO Specialist | Data Scientist | Growth Ninja
With more than 15 years of experience, Loveneet Singh is a seasoned digital marketing director, NLP entity SEO specialist, and data scientist. With a passion for all things Google, WordPress, SEO services, web development, and digital marketing, he brings a wealth of knowledge and expertise to every project. Loveneet’s commitment to creating people-first content that aligns with Google’s guidelines ensures that his articles provide a satisfying experience for readers. Stay updated with his insights and strategies to boost your online presence.
