To access AWS Cloud services, Amazon has provided a simple, scalable, fully managed Elastic Cloud EC2 Instances types. These instances provide complete support to work with advanced applications and tools.
Whatever instance type you make use of, a common data source for workloads allows using multiple instances from more than one server.
It is vital to understand the working of the EC2 instances types keeping the AWS security in mind, along with patching responsibility, key pairs, and various tenancy options.
Through this post, we have made sincere efforts to make you understand about AWS Shared Responsibility Model before and instance-level security within your Virtual Private Cloud (VPC).
Here, we are discussing, how to protect EC2 instances by applying AWS security patches to your instances and multi-tenancy options.
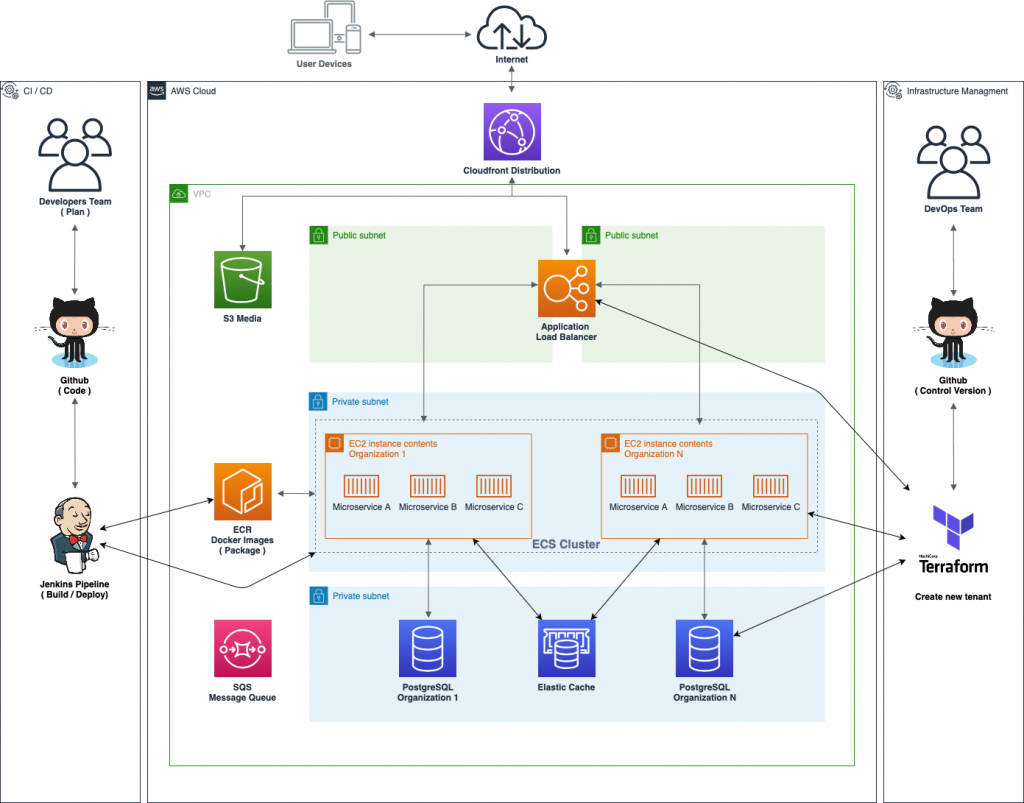
Let’s dive in to learn the fundamentals of AWS services through EC2 instances because that will be required to compute applications and run projects.
AWS security groups and instance security
To provide security at the protocol and port level, AWS security groups (SGs) and EC2 instances play a vital role.
The AWS security groups are like a firewall that contains a set of rules.
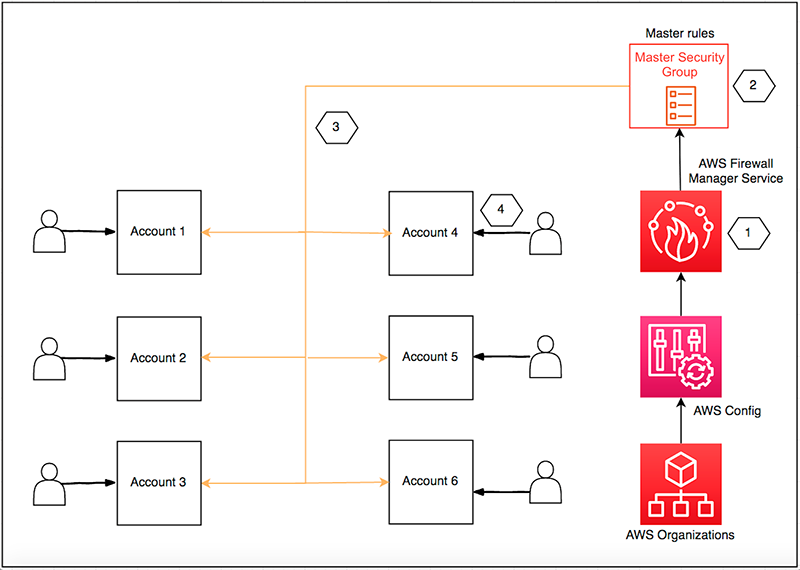
It tracks the traffic coming and going out of an EC2 instance.
Like the network access control lists (NACLs), no deny rules are followed. If a data packet is permitted, it will not be dropped.
When you are accessing the AWS security groups, you have to restrict the data access privileges by making the changes in the permissions. You can develop your security restriction as per the individual need.
However, a guideline by AWS is provided on setting the permissions that clarify data access should be minimum. Only one or two people should be allowed to access the resources.
This is designed so to prevent the security breaches and for the effective use of EC2 instances.
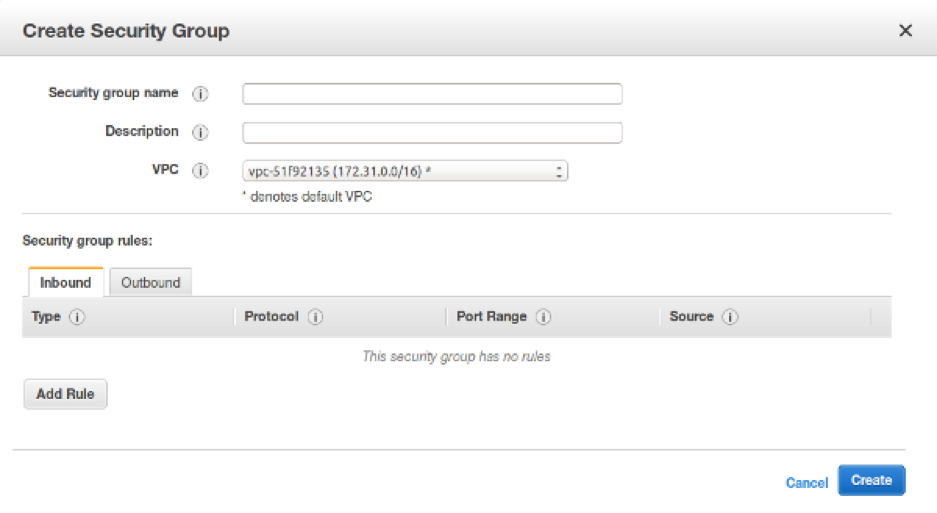
Setting EC2 Instance in AWS
Sign up for AWS
A sign up for Amazon Web Services (AWS) will authenticate you to access Amazon EC2. The payment is taken as per the use.
The new users can start by creating a login as an AWS customer
- To create a new account:
- Open https://portal.aws.amazon.com/billing/signup.
- Follow the online instructions.
- The verification code will be sent to verify your account
Create a key pair
Login information is stored using cryptography. The public key pairs are used to access the EC2 instances type. Once you log in, you get a private key hat that can be used with SSH.
The key pairs can be created from the Amazon EC2 console. For each separate region, you need to create a different key pair for the same instance type.
To create a key pair, you can use one of the following methods.
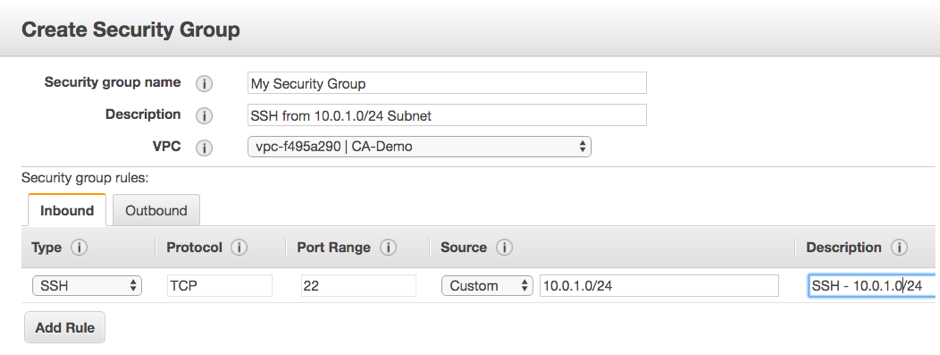
A proper name is given to each security group just to differentiate from one another. The description is optional, but no additional information is needed. Security groups are specific to a VPC.
Note: Choosing a correct VPC will ensure the security of the instances types.
Create a security group
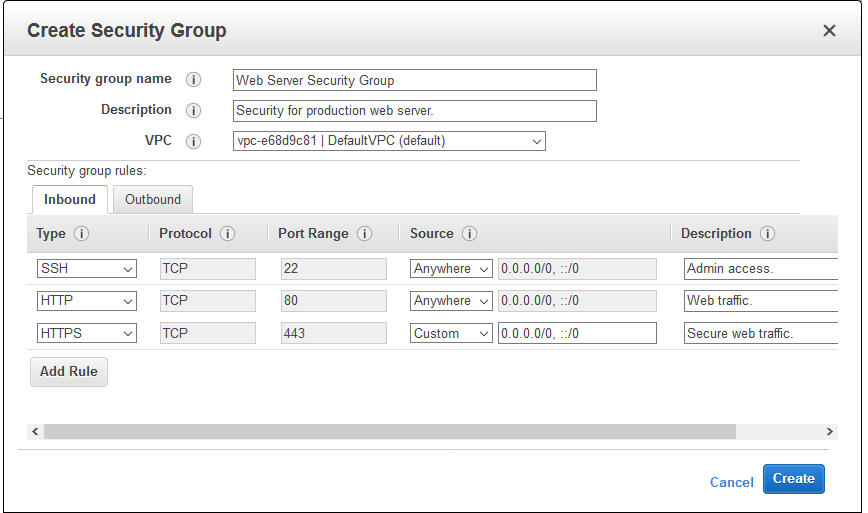
The security groups are an effective way to secure the AWS elastic file system that acts as a firewall for the various instances types.
The rule which you form for the security group will enable you to connect to your instance from your IP address using SSH. You can even apply the rules for giving access through http or https.
Prerequisites
The security group editor in the Amazon EC2 console detects a public IPv4 address to confirm your IP.
In case you are connected through an Internet service provider (ISP) or from behind a firewall without a static IP address, you need to find out the range of IP addresses used by client computers.
AWS security groups: Rules
Inbound and Outbound tables are the source for creating the security group rules.
The AWS security groups have a stateful rule, that allows traffic into an EC2 instance, will automatically allow responses to pass back out to the send.
The outbound process doesn’t wait for an explicit rule in the Outbound rule set.
There are five fields pf each rule:
- Type
- Protocol
- Port Range, Source, and
Description: Both Inbound and Outbound rules follow this ruleset.
Security Group Rules
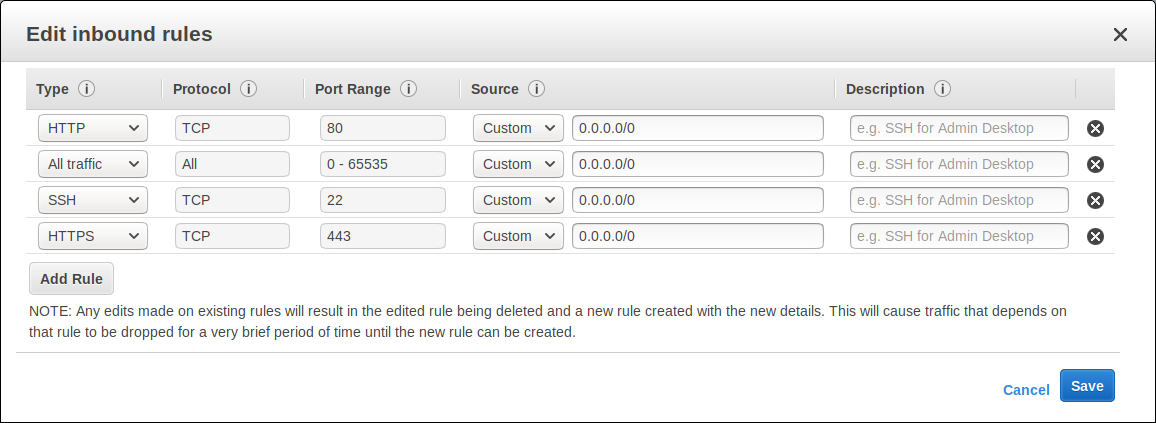
Type: From the list, you can select the protocols like SSH, RDP, or HTTP. You are allowed to select a custom protocol.
Protocol: Here you can specify the protocol details such as TCP/UDP, etc.
Port Range: It takes the default port setting but sometimes you have to use a custom port.
Source: it can be set in a network subnet range with a valid IP address. the access can be left blank to the entire internet using the “Anywhere (0.0.0.0/0)” value.
Description: This field allows you to add a description of the rule that has been added.
Creating a security group
The security groups can be created in different ways such as using AWS CLI or the AWS Management Console. AWS Management Console allows you to create a security group during the launch of an EC2 instance.
Configure Security Group
You can create a security group without EC2 instance, do the following:
- Access AWS Management Console by login
- Choose EC2 service
- Choose “Security Groups” from the available categories on the left
- Create a Security Group by selecting the blue button
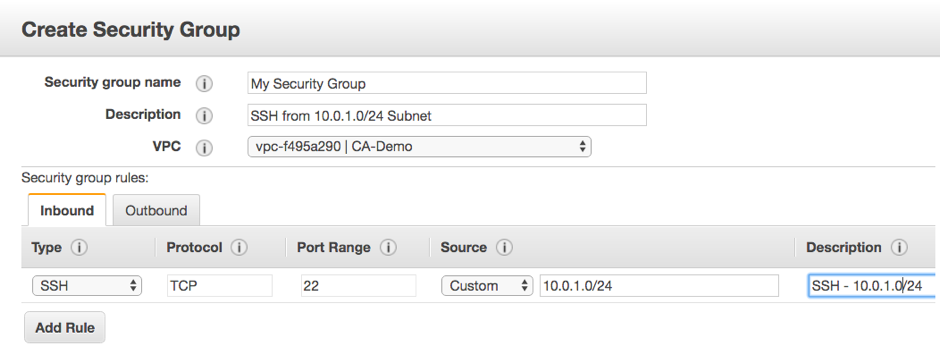
- Provide a name to the security group and give a description
- Choose VPC
- “Add Rule” by using a button
The default limits are set during the creation of security groups. They are
- VPC = 2500 per region
- Rules per security group = 120 (no more than 60 inbound and 60 outbound)
- Security groups per network interface = 5
OS Patch Management
While accessing EC2 instance type , a separate security group is required even if you are accessing a secured AWS.
You have to look for security patches on regular basis. New vulnerabilities and security flaws are being discovered and fixed from time to time.
Moreover, you can’t afford to ignore them as AWS security is the utmost priority to run safe applications.
Once an EC2 instance type is created, patches can be downloaded after checking the details of the patches.
The auto-update feature can be used through the instances used.
For example: yum update -y
Configure Instance Details
The installation of the latest patches provides security to instances types against vulnerabilities and threats. Applying it is a simple yet mandatory process.
Multi-tenancy vs dedicated
Tenancy is related to your host EC2 instances types. To be precise, with your physical server within an AWS Data Center.
During the deployment process of instances, you can specify 1 of 3 tenancy options for your instance:
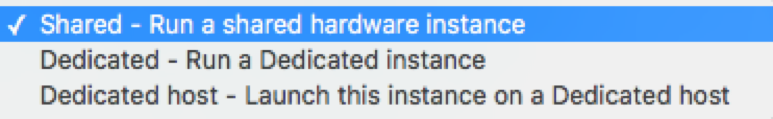
Let’s go through the pros and cons of the same.
Shared Tenancy: This type of tenancy will launch your EC2 instance on available hosts with the required resources to run instance type. This will not have any effect on the other hosts sharing the same instance type.
AWS implements advanced security mechanisms that keeps the two hosts separate while using the same EC2 instance type.
Dedicated Tenancy: Here the tenancy is related to both dedicated instances and dedicated hosts:
Dedicated instances are related to hardware resources used by an individual host. In this case, you have to log in using your AWS account.
This will protect your hardware resources and you are doing it separately for the instances types that you are using because of the AWS internal security policies.
You need to pay extra charges for it as you are restricting other hosts to access the instance type. However, it is not of many benefits as there are hardly any issues regarding hardware security.
On the other hand, dedicated hosts offer additional visibility and control over placing your instances on the physical host.
The different software suites with liceneces can be used such as VM ware, Windows, Linux, etc. The benefit is the ability to use the same host for several instances.
Note: Shared tenancy reduces the overall costs. All instance types can’t get connected through the dedicated tenancy, so if you are thinking of using it, consult the AWS documentation.
Amazon EC2 key pairs and Linux instances
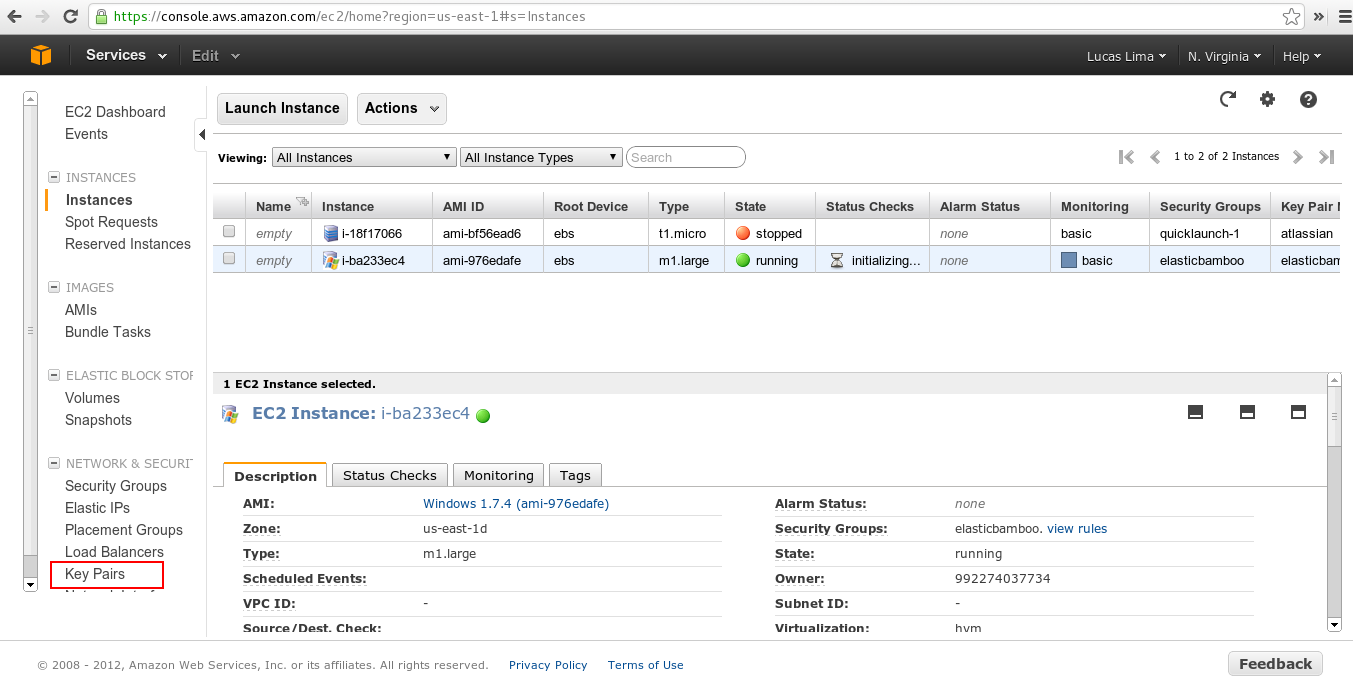
Once everything is set to use EC2 instance type, the question comes as to why key pair should be created and for what it is used for?
As we have already discussed above that a key pair is the combination of a public key and a private key.
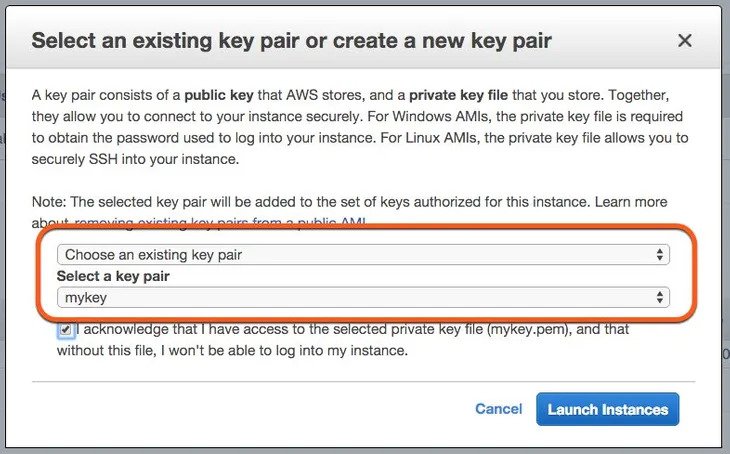
The main function is to provide cryptographic security to secure the instances types.
To refresh from the back, during the creation of an EC2 instance you have downloaded the key pair. We hope that you are preserving that file.
Why we are mentioning this here is because the same key pairs can be used for the multiple instances and you don’t have to create a separate key for every instance type.
For the first time usage of the EC2 instance type, you need to put the detailed information of the keys. Once the access is provided, a simple login will allow you to enter in.
A Closer Review
AWS has made it clear on several occasions that maintaining EC2 instance security is the responsibility of the host.
In such a case, our intention through this post is to make you aware that after getting connected to an AWS security group, don’t leave the chance to become vulnerable to attacks.
You must ensure:
- Deploy a patch management policy during the creation of EC2 instances types.
- Instance tenancy should be decided considering cost and additional security features and needs of the application.
- Finally, manage EC2 instance key pairs by restricting the use of private keys while ensuring instances security.

Director of Digital Marketing | NLP Entity SEO Specialist | Data Scientist | Growth Ninja
With more than 15 years of experience, Loveneet Singh is a seasoned digital marketing director, NLP entity SEO specialist, and data scientist. With a passion for all things Google, WordPress, SEO services, web development, and digital marketing, he brings a wealth of knowledge and expertise to every project. Loveneet’s commitment to creating people-first content that aligns with Google’s guidelines ensures that his articles provide a satisfying experience for readers. Stay updated with his insights and strategies to boost your online presence.
